A Tale of Two Markets: Investigating the Ransomware Payments Economy | August 2023 | Communications of the ACM
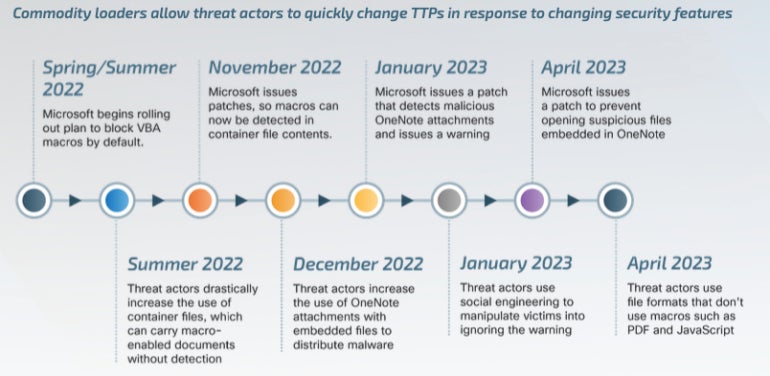
Cisco Talos Report: New Trends in Ransomware, Network Infrastructure Attacks, Commodity Loader Malware

A Tale of Two Markets: Investigating the Ransomware Payments Economy | August 2023 | Communications of the ACM